Biometric Identification System For Access Bisa Information Is Stored On
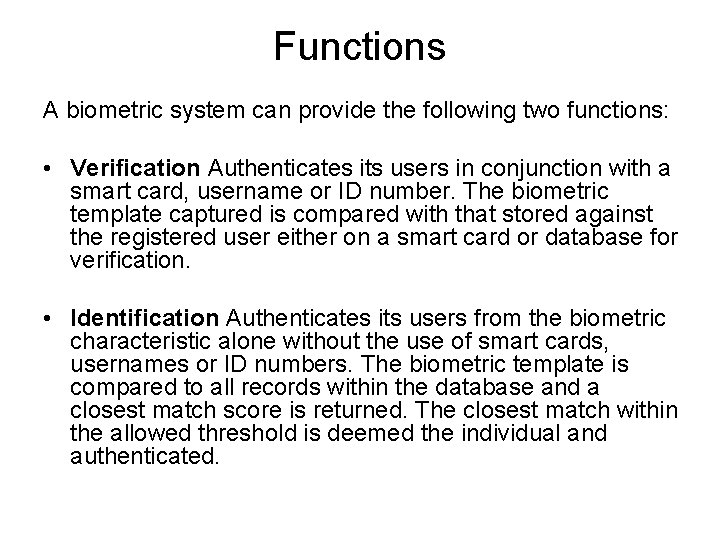
Biometric identification system for access bisa information is stored on. Most of the applicants you process will be given a BISA badge and badge-holders cannot gain access to a US base in Iraq unless the electronic readers at the points-of-entry confirm that the biometric information electronically stored on the badge matches the physical characteristics of the person carrying it. Screens applicants against ABISIAFIS. A system will challenge someone to prove their identity and the person has to respond in order to allow them access to a system or service.
Biometric information is stored on a single device and that device must be presented during authentication for verification purposes. The very best facial recognition software on the market is only ____ effective. Biometric Identification System for Access BISA Collects biometric data and biographical information from all visitors Uses ID Badge and biometric to ensure person is who heshe says they are Vetted against other databases via NPRnet.
Discover the work of forensic analysts in our video. HIIDE is the first step into BISA. Biometric Identification System for Access BISA information is stored on.
Biometric identification system for access BISA is stored on. I3 will train you to. In Iraq and Afghanistan in 2008.
Door alarms are also monitored. Biometric Identification System for Access BISA information is stored on. Biometric authentication asks the question can you prove who you are and is predominantly related to proof of identity in digital scenarios.
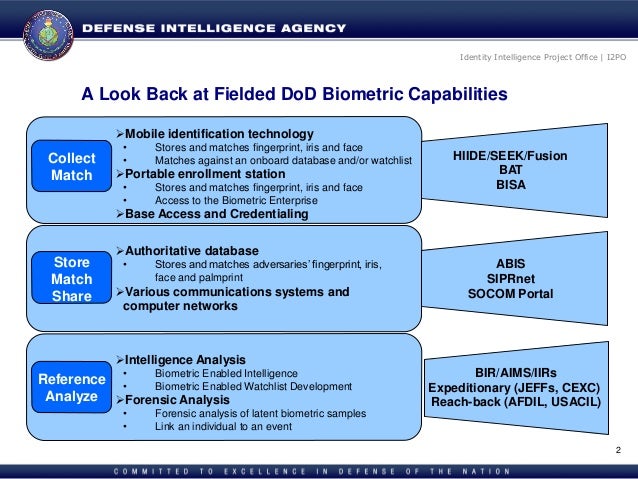
This is most commonly the case on smartphones that use touch ID fingerprint sensors such as Apples Secure Enclave. Today Automated Biometric Identification Systems ABIS can create and store biometric information that matches biometric templates for the face using the so-called mugshot systems finger and iris. As a Biometric Systems Operator with Ideal Innovations Inc I3 you will support US military forces in Iraq by enrolling non-US support personnel Iraqis and others into a computerized base-access system which leverages the very latest biometric identification technologies.
After a suicide bomber infiltrated a high-security US. -Collects iris fingerprint photograph and biographical data.
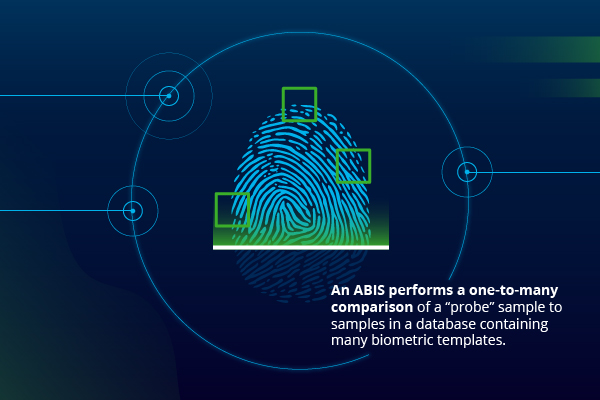
The Biometric Identification System for Access BISA is a force protection initiative that collects multi-modal fingerprint facial and iris biometric information and biographical information.
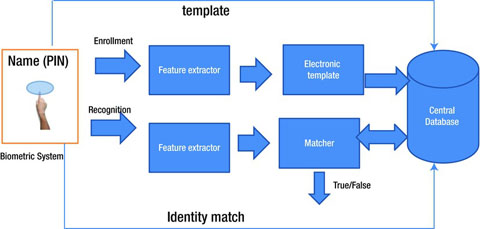
In Iraq and Afghanistan in 2008. Biometric information is stored on a single device and that device must be presented during authentication for verification purposes. They may also be stored on a specialized identity card called a Smart Card. The primary function of a biometric device is to verify or identify registered people on a system. Biometric authentication asks the question can you prove who you are and is predominantly related to proof of identity in digital scenarios. This means that your fingerprint once captured is stored within the token. The Biometric Identification System for Access BISA is a force protection initiative that collects multi-modal fingerprint facial and iris biometric information and biographical information. Discover the work of forensic analysts in our video. Biometric identification system for access BISA is stored on.
In months the Biometric Identification System for Access was serving bases in Iraq. Biometric Identification System for Access BISA Collects biometric data and biographical information from all visitors Uses ID Badge and biometric to ensure person is who heshe says they are Vetted against other databases via NPRnet. Biometric Identification System for Access BISA information is stored on. After a suicide bomber infiltrated a high-security US. Access control requires the ability to authenticate a person and grant or deny access based on time restrictions. Biometric Identification System for Access BISA information is stored on. Biometric tokens tend to be a bit more costly to implement than the alternative because they require both the token and a separate biometric scanner though the added step also adds another line of security to the mix as well.



































Post a Comment for "Biometric Identification System For Access Bisa Information Is Stored On"